Ctrl + F is the shortcut in your browser or operating system that allows you to find words or questions quickly.
Ctrl + Tab to move to the next tab to the right and Ctrl + Shift + Tab to move to the next tab to the left.
On a phone or tablet, tap the menu icon in the upper-right corner of the window; Select "Find in Page" to search a question.
Share UsSharing is Caring
It's the biggest motivation to help us to make the site better by sharing this to your friends or classmates.
Computer Science
The study of algorithms, programming languages, data structures, and computer systems, preparing students for diverse careers in technology and innovation.
algorithm
data structures
programming
software
hardware
operating systems
networking
databases
artificial intelligence
machine learning
cryptography
web development
computer graphics
cybersecurity
robotics
set of typewriter-like keys that enable you to enter data into a computer
- Keyboard
- BlueTooth
- hard drive.
Main drawback of high resolution images?
- Increase in file size
- Increase in pixels
- The quality of Image.
- No drawbacks.
Did you find our presentation informative???
- Yes
- I knew most of the stuff
- Very Informative!! ????
- No
SECONDARY MEMORY IS ALSO KNOWN AS ... (2 ANSWERS)
- input memry
- external memory
- auxiliary storage
what are applications of stack
- recursion
- recursion
- function calling
- tower of hanoi
Which chatting platform is this ????

- Line Chat
- Signal
- Viber Messenger
File sizes are always measured in
- bytes
- bits
- megabytes
- gygabytes
Entering data into a program.
- input
Convert Binary into Denary:0110 1100
- 108
- 107
- 106
- 109
The ____________ business of airlines is flying people and cargo from place to place.
- immerse
- core
- compelling
- unveil
Spot the odd one from the following
- Tim Berners Lee
- Steve Jobs
- Bill Gates
- Linus Torvalds
Social engineering can be also known as ..... attack
- phishing
a device you can use to copy a picture or words from a printed page, onto your computer
- Scanner
Write your name And best friend name
- [No Answer]
A structure diagram is useful for showing the results of which computational method?
- decomposition
____is used for maintenance and configuration of the computer system.
- system utility
Which chatting platform's logo is this ???

- Signal
- Facebook Messenger
- Viber Messenger
Can we off an colour pictures are file effect
- Background
IF THE INPUT IS 1, THE OUTPUT IS 0:
- NOT gate
- XOR gate
- OR gate
- And gate
Input Devices exmaples.
- [No Answer]
WHAT IS MEMORY BUS?
- When input devices send binary data to a CPU, it immediately stores that data
- Memory is designed for fast access and typically stores only the data and instructions that are necessary for the currently running programs on a computer
- Computers also vary a lot in memory size, usually because of physical size constraints.
- High speed communication transfer system, made from wires, conductors, or optical fibers
Which of the following software can’t be categorized as application software?
- VLC
- Imovie
- AVAST
- MS word
One characterstic that explains DDoS attack
- Its purpose is disrupt normal traffic on a network
- the attacker's goal is to take control of a network
- When attacker takes control of network is called botnet
- All above correct
- None above correct
What is an Image Resolution?
- Number of pixels in an image.
- Number of bits in an image.
- Number of bytes in an image.
- Number of data in an image.
What is the name of the chatting platform in the picture ???

- Chat Port
- Snapchat
- Podium Webchat
- Telegram
The Website address is called URL.
- True / False
How many years after the death of a creator dies the Copyright, Designs and Patents Act last?
- 70
Difference Between RAM and ROM?
- [No Answer]
Convert negative denary into Binary in two's compliment format:-67
- 1011 1101
- 1011 1111
- 1010 1111
- 1100 0011
A web page is a document with only text.
- True / False
Which people were allowed to use the 1st generation of computers?
- Engineers
- Computer Engineers
- Millitary enginners
- Goverments
Find the odd one out from the following
- Joystick
- Scanner
- Printer
- Keyboard
Some consequences that cyber-attacks can produce ( 3 options are correct)
- Loss of privacy
- Loss of privacy
- Establish new social contacts
- Security breach technology
- New alternatives to share different information
- Shows how vulnerable are my data online
_Select all the things an organisation must do if they collect your personal data.(according to the Data Protection Act)
- keep the data accurate and up to date
- keep the data accurate and up to date
- it must not be kept any longer than necessary
- must not be transferred to other countries
Button are used to cut a launch and actions in your presentation
- Sideshow
- Action
- None
Choose correct answers
- LED (Light emitting diode) - OUTPUT
- LED (Light emitting diode) - OUTPUT
- pH sensor - OUTPUT
- moisture sensor - INPUT
Which button should be clicked to reduce a window on the taskbar?
- Minimize
- Maximize
- Restore
- Close
... is the repetition of a process.
- iteration
-contains the circuitry and hard drive for the computer. It is the brain of your computer and controls and processes all the information you input into your computer. It also directs and controls the flow of information back out of your computer.
- CPU
- Hard drive
- Bluetooth
- computer
What is the other name used for computer programs and information?
- OutPut
- Process
- Software
- CPU
Output obtained on paper using a printer is called...
- Paper Copy
- Hard Copy
- Soft Copy
- None of these
In order to connect your computer to the Internet with a modem, your computer will have to have a(n) ________ port
- HDMI
- USB
- Headphone
- Ethernet
In which year was internet and television launch in Bhutan?
- 1979
- 1969
- 1999
- 1989
What is an algorithm?
- A step by step set of instructions for completing a specific task
- Guidelines to help you do your job
- Rules of thumb for a profession
- Principles to live your life successfully
Since computers are not capable on understanding human language programs, it is translated into machine code known as...
- Binary Code
- Programming Language
- Computer Instructions
- Language Code
what is the first step for enginnering design process?
- Imagine
- Plan
- Identify
- Create
- Communicate
... compression algorithms reduce the size of files without losing any information in the file, which means that we can reconstruct the original data from the compressed file.
- BITMAP
- COMPUTER
- LOSSLESS
- LOSSY
The full form of ARPANET is
- Advance Research Projects Agency Network
- Advanced Research Projects Agency Network
- Advanced Research Projects Argency Network
- Advanced Research Peoples Agency Network
You always have to use outline before you print a document.
- True / False
KEY TERMSThe things that are actually right and wrong, things are passed and enforced to help protect the users of computers.
- ethical
- legal
- cultural
- environmental
What did you know about secondary storage?
- [No Answer]
_Select all the penalties of breaking the Copyright, Designs and Patents Act
- £3000
- up to 1 year of imprisonment
- up to 10 years of imprisonment
- £5000
The very first network connections re-used the ... of telephone lines, communicating binary data via pulses of electricity.
- iron cables
- steel cables
- copper cables
- CAT-5E cable
queue is based on the principle
- FIFO
... is the process of converting one data type to another.
- casting
A PC has a total storage capacity of 500 GB. How much storage capacity will the same PC have in terms of MB.
- 5000000 MB
- 50000 MB
- 5000 MB
- 500000 MB
2 types of IP addresses?
- IPv4 and IPv6
- IPv4 and IPv8
- IPv3 and IPv6
- IPv9 and IPv10
File size of an image is calculated as:
- Image resolution (in pixels) x colour depth (in bits)
- Sample rate x sample resolution x length of sample
- Image resolution + colour depth
- Image resolution - colour depth
Human mistakes in the accessing of online services occur because (3 options are correct)
- Clicking on unsafe links
- Clicking on unsafe links
- Sharing confidential information
- Opening unknown attachments
The text in the document can be divided into columns
- Single
- Multiple
- Double
Convert Binary into Hexadecimal:1011 1110 0001
- CE2
- 6ED
- BE1
- 9G2
All the following statements of WWW are true except
- It was invented by Tim Berners Lee
- It was invented by Sergey Brin & Tim Berners Lee
- WWW stands for world wide web
- WWW is the first website
What is pseudocode?
- machine code
- high level programming language
- low level programming language
- An algorithm expressed in human language that looks like programming code
Shift this Binary 3 places left:0001 0101
- 1010 1000
- 1000 1010
- 0101 0100
- 0000 1111
HTH...?
- Hope to Help
- Hope That Helps
- Hope that Hurts
... are techniques that reduce file size by discarding the less important information.
- bitmap compression algorithms
- image compression algorithms
- lossy compression algorithms
- lossless compression algorithms
She came to the party wearing an ______________ costume and blond wig.
- clanky
- outlandish
- overwhelming
- cluttered
_Select all the penalties for breaking the Data Protection Act
- warnings sent to the organisation
- warnings sent to the organisation
- ordering the company to comply
- a fine of 4% of the company turnover
What is computational thinking?
- To think like a machine
- To describe a problem in a way so that it can be solved with computational methods
- To think like a computer
- To think mathematically
What is the name of the computational technique which involves breaking down a large complex problem into smaller and simpler sub problems until each part of the problem can be solved computationally?
- abstraction
- decomposition
- flow diagram
- structure diagram
BRB...?
- Best Regards
- Be Right Here
- Be Right Back
a member of the group of animals that includes humans and monkeys
- primate
WITH 8 BITS YOU CAN STORE NUMBERS BETWEEN ... AND ...
- 1-255
- 1-100
- 0-255
- 0-100
Choose among the programming languages that has specific purposes.
- Java
- Python
- CSS
- HTML
device that reads information from a CD or DVD onto your display screen and/or your speakers
- CD
- Bluetooth
- curser
- computer
Top down design, heirarchical structure idagram and tree diagram are all connected with representing the results of which computational technique?
- decomposition
- abstraction
- pattern recognition
- pseudocode
Internet is known as ________in Dzongkha
- གློག་རིག་ཡོངས་འབྲེལ།
- ཡོངས་འབྲེལ།
- གློག་རིག།
- རྒྱང་བསྒྲགས་ཡོངས་འབྲེལ་ལྟ་བུ།
By looking at the picture guess which chatting platform it is.....

- Podium Webchat
- Chaport
- Instagram Messenger
- Youtube live chat
When you present an algorithm graphically as a flow diagram, what shape do you use to represent selection?
- reectangle
- diamond
- platinum
- oval
Convert Denary into Binary:254
- 1111 1100
- 1110 1111
- 1010 0101
- 1111 1110
a movable indicator on a computer screen identifying the point that will be affected by input from the user, for example showing where typed text will be inserted.
- Cursor
The instructions that we feed to the computer that allows it to complete a specific task is known as...
- Program
- Binary Code
- System
- Programming Language
The club has ................. plans to build a new stadium.
- unveiled
- immersed
- captivated
- blasted
The first message "LOGIN" using the ARPANET was sent from
- UCLA to Stanford in North America
- Stanford to UCLA in North America
- UCLA to Stanford in South America
Which of the following groups have only input devices?
- None of these
- Mouse, Keyboard, Monitor
- Mouse, Keyboard, Scanner
- Mouse, Keyboard, Printer
It is difficult for humans to translate Human Language Programs into Machine Code or Binary Code. Hence, programmers use ___ ___ that translates our Programs into Computer Language easily.
- Programming Language
Tortillas are a .................. of Mexican cooking.
- infancy
- endeavour
- staple
- premise
Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/0af942a8-43e0-4273-b0b0-736ebad9fd3c?w=200&h=200

- 0
- 1 1
- 1 0
- 1
stack is based on
- LIFO
- FIFO
- LFIO
- FILO
'Multimedia' has been a .................... in the computer industry for years.
- buzzword
- spin
- grab
- jar
What does CPU do?
- Does decision making
- Does decision making
- Does data programming
- Has a variety of commands
What are the main Components of MS Word?
- [No Answer]
This is a permanent memory chip inside your computer. ROM has all the information a computer needs to tell it how to run.
- Read Only Memory
The background of the desktop is called...
- BackGround
- ScreenSaver
- WallPaper
- None of these
Charles Babbage was born in
- England
What is 'benchmarking?
- A test used to measure the amount of memory that a computer has.
- A test used to measure the number of cores in a CPU.
- A test used to measure the performance of a computer .
In the "early days", what was a computer
- A machine that did calculations
- A slave
- A person who did calculations
- A person who used machines
What does this do?

- Maximize
- Minimize
- Hide
- Open a window
It is clear that most common cyber-attacks occur because of the.... (2 words)
- human errors
Which type of loop repeats until a condition is met?
- for loop
- count controlled iteration
- while loop
- condition controlled
______________ your foot in ice cold water to reduce the swelling.
- usher
- immerse
- pan
- dime
KEY TERMSHow groups of people of particular beliefs, practices or languages may be affected by a particular situation concerning the use of computers/technology.
- ethical
- legal
- cultural
- environmental
The intersection of a row and column is called a
- [No Answer]
-another term for display screen
- Monitor
_Select all the types of operators:
- /
- /
- *
- +
- -
- %
Which of these is an operating system?
- Dell
- Windows XP
- Yahoo
- Microsoft
________was the first person to send an electronic email in 1971.
- Ray Tomlinsun
- Ray Tomllinson
- Ray Tomlinson
WHICH OF THE FOLLOWINGS IS NOT RELATED TO BINARY DATA
- TRUE - FALSE
- 0 - 1
- YES - NO
- DO - DON NOT
Net stands for_______
- network organization
Maximum number of columns in a table can be
- 53
- 63
- 74
Which chatting platform is this ???

- Skype for Bussiness
- Facebook Messenger
- Signal
The following image represents..... attack
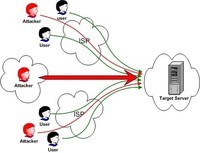
- MitM
- Phishing
- DDoS
- Password attack
- None above correct
CPU stands for?
- [No Answer]
By looking at the picture guess which chatting platform it is....

- Chaport
- Telegram
- Online Viber Messenger
- Kahoot Quiz Chat
The most used virus protection software is...
- Windows Firewall
- AVG
- McAfee
Give Output devices Examples.
- [No Answer]
LEGISLATIONThis act looks after the personal data of people.
- Data Protection Act
-small, portable device using flash memory to store data, ranging in capacities from 64 MB to over 1 TB.
- CD
- DVD
- Flash drive
- Computer.
Type the following translation of His Majesty’s Address to the Nation on the 114th National Day into your answer box within the given time period. "On the auspicious occasion of our National Day, I offer my deep prayers to Guru Rinpoche, humble reverence to Zhabdrung Ngawang Namgyal, and profound gratitude to His Majesty the Fourth Druk Gyalpo. I extend my heartfelt Tashi Delek to the people of the 20 Dzongkhags and Bhutanese living abroad. Despite the threats from the Covid-19 pandemic, we have continued to successfully pursue our national goals. This is due to the blessings of the Triple Gem, the good fortune of our leaders, the merit of our forefathers, and the unified efforts of our people.Today, our Nation stands secure and peaceful. Yet, the foremost question in our people’s minds is when the pandemic will end. While it is difficult to provide a definitive answer, the most important task ahead is for us to remain fully prepared and vigilant. "

- [No Answer]
In what year was the Data Protection Act passed?
- 2018
Response from the program.
- output
Convert Denary into Hexadecimal:2004
- DE4
- 7D4
- BE4
- 65D
Description on secondary storage(true or false)
- Accesibble to CPU
- Not accesible to CPU
- Enables permenant storage
- Enables temporary storage only
4 Things common to all computers
- INPUT, STORAGE, POWER MANAGEMENT, OUTPUT
- INPUT, EXECUTE, PROCESSING, OUTPUT
- INPUT, STORAGE, PROCESSING, OUTPUT
- DATA TYPE, STORAGE, PROGRAMMING, OUTPUT
_Select all the examples which are protected by the Copyright, Designs and Patents Act
- artwork
- artwork
- ideas
- music
- films
In a flow diagram what does a parallelogram shape mean?
- A decision
- A loop
- A sequence
- input or output
_____ is a way of repeating code
- While
- Expression
- Loop
- Lopp
What is the Extension of MS Word file?
- [No Answer]
............... forces have taken control of cities in the north of the country.
- dreadful
- Hostile
- cognitive
- exquisite
A ___ is the basic unit of all computing memory storage terms.
- bit
ON-OFF STATE OF A SINGLE WIRE IS CALLED
- BIT
Computers use ... to transform the 1s and 0s from input wires.
- ELECTRICITY
- TRANSISTORS
- LOGIC GATES
- WIRES
For the simplest of images, computers can use a compression algorithm called
- file size compression
- image compression
- run-length encoding
- bitmaps
System software can be classified into
- 5 types
- 3 types
- 2 types
- 4 types
IN DECIMAL NUMBETR SYSTEM WE HAVE DIGITS FROM ... TO ...
- 1 - 10
- 0 - 9
- 1 - 100
- 0 - 99
Which Persian scientist is the word 'Algorithm' named after?
- Archimedes
- Xerxes
- Al Khawarizmi
- Al Jabra
Sound waves are analogue data. Computers cannot work with analogue data. So what is need to be done in order for computers to store sound waves.
- Sound waves need to be sampled.
- Sound waves need to be sampled.
- Can do this by ADC
- (Analogue to Digital Converter)
What should you do after making your model
- Get feedback on it
- Improvise it
- Consider your possibilities
- Make a newer model and give it to your client.
is used to hold programs and data you put into a computer while it is on. Once you turn your computer off, any information in RAM will be erased and lost forever. Therefore, you MUST save your data to a hard drive or flash drive before turning your computer off.
- Random Access Memory
SERIES OF COMMANDS
- PROCESSING
- FUNCTION
- STORAGE
- ALGORITHM
In ... the next statement to be executed depends on whether the condition being tested is True or False.
- _selection
Internet is also referred as_______
- net
A part of the program which causes it to operate incorrectly. The error does not prevent the program running but it does not produce the expected output.
- logic error
When your document is in print layout, it looks exactly as it’s going to be printed.
- True / False
What software is this?
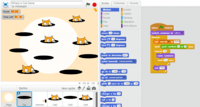
- Scratch
- Sketch-up
- Pages
- Kodu
the bulk of the memory of a personal computer that is magnetically stored on hard disks that constitute the hard drive. Information in the hard drive is durable, in that it remains magnetically stored when the computer is turned off. **everything you save unless you save to a disk or a jump drive*
- Hard Drive
- CPU
- BlueTooth
impossible to believe and really unlikely is far-...............
- fetched
The cyber-attack in which attacker intercepts communication between two hosts..
- mitm
Which of the following is not a pointing device?
- Keyboard
- Mouse
- Joystick
- Light Pen
Convert Hexadecimal into Binary:45A
- 0100 0101 1010
- 1011 1111 0000
- 1001 0011 0110
- 0100 0101 1011
output device that prints text or illustrations on paper
- Printer
A______________________ is an artificial intelligence (AI) software that can simulate a conversation or a chat with a user in natural language through messaging applications, websites, mobile apps or through the telephone.

- Chat Bot
What does input do?
- releases or conveys information
- Holds memory for short periods of time
- It does desicion making
- Input helps you put in data to your computer.
a tiny physical device that acts like a digital switch in computers
- MODEM
- SWITCH
- UPS
- TRANSISTOR
a program or piece of software designed and written to fulfill a particular purpose of the user.
- Application
Bitmap images are made up of ______
- Pixels
Define 'Home Tab' in MS Word.
- [No Answer]
... are sent to a user's computer from websites, thy allow a website to store data about your browsing, remember you are logged in, track you and target your advertising. They must be consented to.
- cookies
Do a fill in for imagine
- Consider all possibbilites that can happen
All sites in your presentation used a background
- Black
- White
- None
Which chatting platform's icons are these ???

- Signal
- Skype
- Yahoo Messenger
A ...................... $3 trillion was spent in building the U.S. nuclear arsenal.
- pervasive
- staggering
- cluttered
- agitated
Convert Hexadecimal into Denary:45A
- 1234
- 4321
- 1114
- 6969
... is a set of instructions that follows on one after another.
- sequence
In what year was the Copyright, Designs and Patents Act passed?
- 1988
a film which is extremely upsetting is har___________
- rowing
Which is a mobile operating system developed by Apple?
- AOS
- EOS
- UOS
- IOS
The computer Hardware can be classified into
- 2 types
- 3 types
- 5 types
- 4 types
A ... is a name for a memory location used to store data that can be changed.
- variable
Choose among the Programming Languages Example that does have general purposes.
- Java
- Java
- Python
Who can edit the material, under the Copyright, Designs and Patents Act?
- the owner
- the owner
- anybody
- someone with permission
Which type of loop repeats a given number of times.
- for loop
- for loop
- count controlled iteration
Which generation were when computers became portable.
- 1st gen
- 3rd gen
- 4th gen
- 5th gen
Add the 2 Binaries:0010 0111and0100 1010
- 1001 0101
- 0111 0001
- 1011 1111
- 0001 1000
microcomputer that's often used by hobbyists to create projects like animated LED displays or bird watchers
- Arduino Uno
- Macintosh
- Android
- Raspberry PI
KEY TERMSHow we impact the natural world, E-Waste, sustainability, recycling and energy demand, are issues regarding technology.
- ethical
- legal
- cultural
- environmental
This memory is for short-term storage and is lost when the computer is turned off.
- Icon
- CPU
- Hard Drive
- RAM
A MAC address is usually made up of how many bits?
- 48
- 32
- 64
- 128
One characteristic that explains the term cyber-attack would be:
- Cybercriminals using one or more computers against other computer producing some damages.
- A single plan to produce damage
- Damage produced to a computer in a netwrok
- Act of steal private data
Bhutan Telecom launched the first mobile communication service in the country.
- 2001
- 2003
- 2002
- 2000
GTR...?
- Got To Read
- Got To Race
- Got To Run
What is the difference of the 1st generation of computers to the 2nd generation of computers.
- Smaller
- Bigger
- Speed in micro seconds instead of milliseconds
- Speed in nano seconds instead of picoseconds
Which country's chatting platform is this ????

- Kuwait
- Kosovo
- Korea
- Kenya
A ... is a location in memory, the value CANNOT be changed.
- constant
Trojan horses, spyware and viruses are examples of.....attack
- malware
What is the name of the computational method where you remove unnecessary details to create a simpler focused representation of a problem or situation?
- abstraction
KEY TERMSThe things that are considered right and wrong, it consists of the standards of behaviour that are acceptable within society, they are the moral principles and values.
- ethical
- legal
- cultural
- environmental
The number of bits used to represent each color is called the ____________
- Colour depth
a device that controls the movement of the curser or a point on the display screen. It is a small object you lay on hard, flat surface
- Mouse
Image: https://quizizz.com/media/resource/gs/quizizz-media/quizzes/08ddecff-732d-4286-8cf8-89a37fd982f7?w=200&h=200
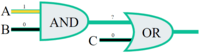
- 1
- 1 0
- 0
- 0 1
Head and shoulders are area in the top and bottom of each page
- Margins
- Cell
Hexadecimal number system is a base __ system
- 16
The air was full of ..................... smells of flowers and freshly cut grass.
- immerse
- primate
- sentient
- evocative
Futures find and correct that spellings and Zama arrows
- Spelling and grammar
- Head has folders
- Both a and b
One of the following is not a cyber-attack
- MitM
- ADToS
- Phishing
- DDoS
- Malware
NVM.....
- Never Mind
- Not Very Much
the process that professionals use to write code that instructs how a computer, application or software program performs
- keyboard
- Programming
- CD
- Bluetooth
Why are comments used?
- to make comments about the code
- to send messages between programmers
- to explain key functions and key sections
- to explain the code for the users
While her husband had affairs with other women, she lived in ................. ignorance.
- overwhelming
- tactile
- blissful
- outlandish
to play it by ___________ means to improvise
- ear
Two characteristics of password attack
- it does not requiere any maliciuos software to run
- it does not requiere any maliciuos software to run
- It can spy on your computer activity without your permission.
- Process of recovering passwords from stored data
Is a word processor package from Ms Office
- MS Word
- MS PowerPoint
- Table
Every component of your computer is either
- Input devices or output devices
- Application software or system software
- Software or CPU/RAM
- Hardware or software
What is meant by sampling resolution (bit depth)?
- The number of bits per sample.
- The number of bytes per sample.
- The number of pixels per sample.
- The number of data per sample.
_Select all the rights you have, according to the Data Protection Act
- the right to view your data for free
- the right to view your data for free
- the right to be forgotten
- must consent to having marketing sent to you
- the right to withdraw consent
- the right to change inaccurate data
What symbol is used for commenting?
- #
This is called...?

- switch case
In a flow diagram, how do you show iteration (loop)?
- Arrows pointing back to a previous step
- more than one arrow exiting a diamond shape
- Arrows pointing forward skipping some steps
- a parallelogram
BTW...?
- By The Way
- But Then Week
- By To Way
All the evidence points to dreaming being a highly complex ..................... activity.
- gripping
- evocative
- cognitive
- overrated
the shortwave wireless interconnection technology for mobile devices.
- Bluetooth
IB...?
- I'll be back
- I'm Back
- I am Broke
_____is referred as two or more computers are connected with each other.
- network
An ... allows multiple items to be stored under one variable name, this reduces the need for multiples variables.
- array
Which of these actions does primary storage do?
- Holds memory for long periods of time while the computer is down.
- Works only when the computer is running.
- Works when the computer is down
- Works only when computer is running
"CTRL+ N" in MS Word.used for.
- [No Answer]
Convert negative binary numbers in two's compliment format into Denary:1001 0011
- -246
- -109
- -69
- -108
Which of these is not a way to represent an algorithm?
- Flow chart
- Pseudocode
- machine code
- mind map
To keep up this site, we need your assistance. A little gift will help us alot.
Donate- The more you give the more you receive.
Related SubjectEuclidean Algorithm
Programming Logic and Design
Computer Programming 2
Quantum Computers
Programming vs Coding
Origin of Women in Computing
Software Development
Mechatronics
Computer Information Systems
Computer Numerical Control
Introduction to Computing
Introduction to Multimedia
Database Management System
Data Structures and Algorithms
Computer Fundamentals
3D Game Art Development
Next Generation Kindle
Apple M4 Macs
Apple Intelligence: Transforming Our Digital Experience
Quality Assurance Testing
Driver Device
Computer System
Computer Support Technician
Desktop Publishing
Programmable Logic Controller
Managing Information and Technology
Information Technology Capstone Project
Intro to Hardware Description Language
Information Systems Operations and Maintenance
Animation Project
Computer Programming
Modeling and Simulation
Operating System Functions
Linux Administration
Entrepreneurship Information
Network Administration
Learning Communities
Work Immersion
Professional Salesmanship
Discrete Mathematics
The Contemporary World
Application Development and Emerging Technology
Introduction to Machine Learning
Number Theory
Web Enhanced Animation Graphics
Cyber Security: Theories and Practice
2D and 3D Digital Animation
Intrusion Detection System
Professional Ethics in Information Technology
Network Security
Manufacturing Technology
Industrial Electronics Maintenance
Show All Subject
Affiliate Links
Shopee Cashback Voucher
Temu $0 Shipping Fee
Amazon 75% Off Discounts